Software Solutions
We develop custom software solutions by considering the unique needs of each business. In the embedded software field, we offer efficient and customized solutions that work integrated with hardware.
- Web and Mobile Application Development: We provide support in the processes of designing, developing, and launching customized web-based and mobile applications according to the needs of businesses, individuals, or organizations.
- Integration Solutions: We offer technical solutions developed to ensure seamless operation between systems, devices, or platforms of businesses. Integration solutions play an important role in increasing business efficiency, automating processes, and optimizing data flow for effective process management.
- Embedded Software Development: It encompasses the processes of developing, implementing, and maintaining software designed to perform specific functions on electronic devices and systems. It can be customized according to your embedded system requirements and used in various sectors (automotive, healthcare, industrial automation, consumer electronics, defense, etc.). We provide consulting and support in Embedded System Design and Development, Firmware Development, IoT and Smart Device Integration, Software Testing and Verification, Protocol Development and Integration, Embedded Artificial Intelligence and Machine Learning.
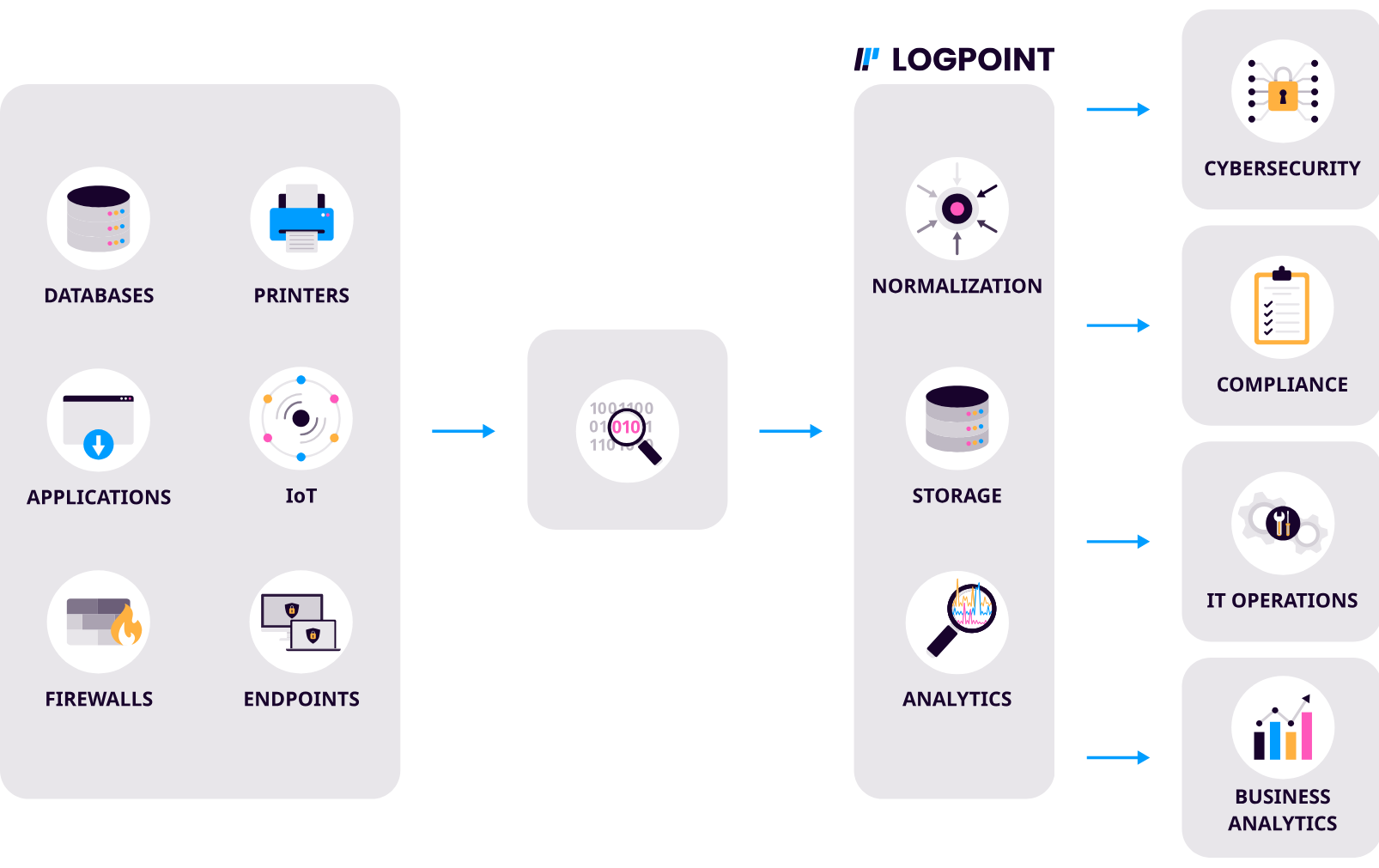
- Cyber Security Solutions: It is the set of techniques, processes, and technologies used to protect digital assets (information, systems, networks, and devices). We provide support in the areas of security vulnerabilities of institutions by ensuring information security against unauthorized access, data theft, attacks, and other cyber threats, guaranteeing the continuity and confidentiality of systems. We carry out activities in Intrusion Detection and Prevention (IDS/IPS), Penetration Testing (Pentest), Data Security, Identity and Access Management (IAM), Threat Intelligence and Monitoring, Security Policy and Compliance, Incident Response and Recovery, IoT and Industrial Security.